The Middle East and North Africa (Mena) region has seen an unprecedented 236 per cent surge in distributed denial of service (DDoS) attacks during the second quarter of 2025, driven largely by escalating geopolitical conflicts, according to a new report from cybersecurity firm StormWall.
The surge marks the highest number of attacks ever recorded in the region’s history, with hacktivist groups accounting for 73pc of all malicious traffic. The report states that government infrastructure bore the brunt of these attacks, fuelled by tensions stemming from the Israel-Palestine and Iran-Israel conflicts.
StormWall, which operates dedicated scrubbing centres in the Middle East with a combined filtering capacity of over 5 terabits per second (Tbps), analysed attack patterns across its regional network to compile the data.
The analysis reveals a significant shift in both the scale and sophistication of cyberattacks. The number of API-layer attacks increased by 162pc, while probing attacks – used by hackers to find system vulnerabilities before a full-scale assault – saw a ninefold rise.
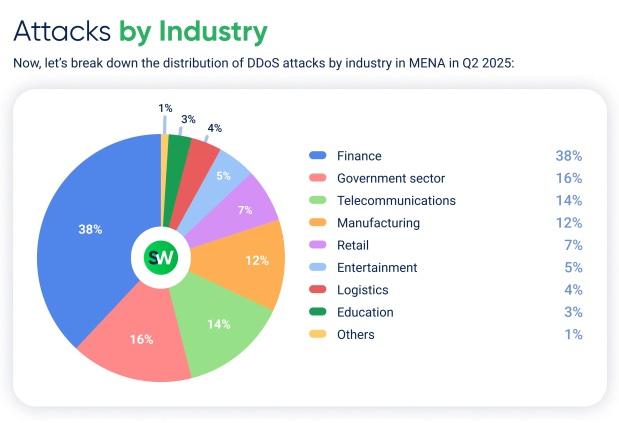
The financial sector was the most targeted industry in Mena, absorbing 38pc of all cyberattacks. This represents a 26pc increase in attacks against the sector compared to the previous year. Government services were the second most attacked, with a 16pc share and a 53pc increase, followed by the telecommunications sector at 14pc.
Geographically, Saudi Arabia was the most targeted country, accounting for 22pc of all attacks. Israel’s share of attacks jumped from 11pc in the first quarter to 19pc in the second, while Iran’s share increased slightly from 16pc to 17pc.
The report highlights a growing sophistication in attack methods. While traditional attacks rely on overwhelming traffic volume, API attacks are becoming more precise and efficient. According to the data, API attacks generated an average of just 4.7 gigabits per second (Gbps) of traffic but were still capable of taking down targets using only 12pc of the traffic volume required for traditional floods.
Most API attacks used botnets composed of approximately 140,000 compromised devices. The most common method for targeting APIs were hypertext transfer protocol (HTTP) floods, accounting for 48pc of all such attacks.
“Attackers used to rely on a lot of traffic, but now they’re going after specific targets,” said StormWall’s founder Ramil Khantimirov. “This takes 88pc less traffic to have the same impact. It has become very important to review and update DDoS defences to maintain a good security posture.”
avinash@gdnmedia.bh


&uuid=(email))